Introduction
In the era of digitalization, data security has become a crucial aspect, especially when it comes to sensitive information. Cryptography, an established field of study, plays a pivotal role in ensuring data security. Hash functions, which generate a fixed-size output for an input of any size, are the building blocks of many cryptographic applications.
SM3 Hash is a robust and secure hash function developed by the Chinese Government in 2010. In this article, we will dive deep into SM3 Hash, its features, and its applications in various scenarios.
Understanding SM3 Hash
SM3 Hash is a cryptographic hash function similar to SHA-3. However, it has different design principles, and it targets specific security requirements. SM3 Hash follows the Merkle-Damgard construction, which divides the input message into blocks and applies a compression function to each block iteratively.
The SM3 Hash output is a 256-bit fixed-size digest. It provides collision resistance and pre-image resistance, ensuring that no two distinct inputs can produce the same digest, and it is computationally infeasible to determine an input message from its digest.
How SM3 Hash Works
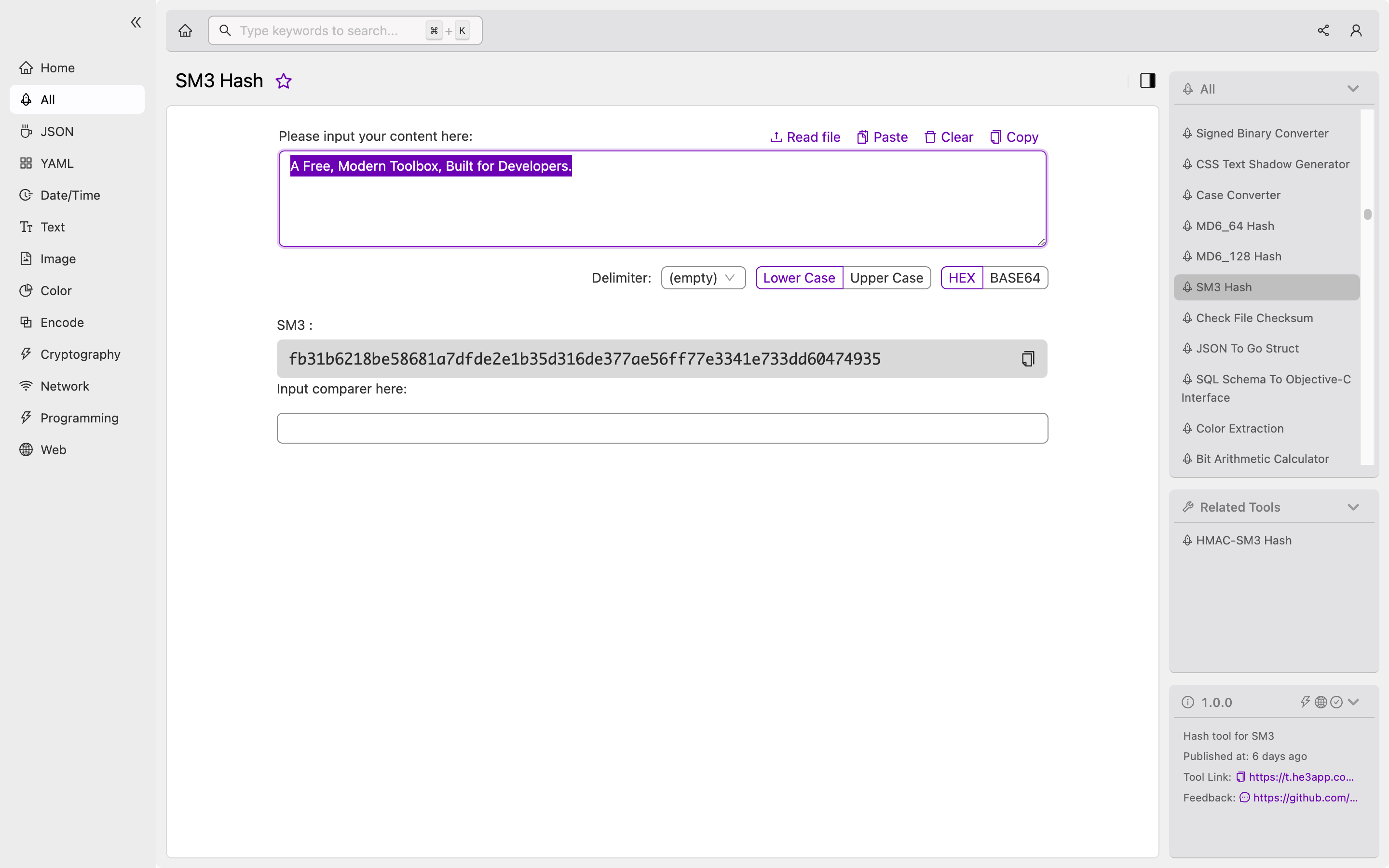
Or you can use SM3 Hash tool in He3 Toolbox (https://t.he3app.com?dly3 ) easily.
SM3 Hash has four stages: message padding, message expansion, compression function, and finalization.
-
Message Padding: SM3 Hash pads the input message to meet the required length. The padding length varies according to the message length, and it ensures that the message length is a multiple of 512 bits.
-
Message Expansion: SM3 Hash divides the padded message into 512-bit blocks and expands each block into 132 words of 32 bits each.
-
Compression Function: SM3 Hash iteratively applies the compression function to each expanded block. The compression function processes each block and updates the intermediate hash value.
-
Finalization: SM3 Hash combines the intermediate hash values to produce the final hash value.
Key Features of SM3 Hash
SM3 Hash has several key features that distinguish it from other hash functions. The following table lists some of SM3 Hash’s key features:
| Feature | Description |
|---|---|
| 256-bit Digest | The SM3 Hash output is a 256-bit fixed-size digest. |
| Collision Resistance | SM3 Hash provides collision resistance, ensuring that no two distinct inputs can produce the same digest. |
| Pre-image Resistance | It is computationally infeasible to determine an input message from its digest. |
| Iterative Compression Function | SM3 Hash applies the compression function iteratively to each block of the input message. |
| Message Padding | SM3 Hash pads the input message to meet the required length, ensuring that the message length is a multiple of 512 bits. |
Scenarios of Using SM3 Hash in Development
SM3 Hash has numerous applications in various scenarios. Some common scenarios where SM3 Hash is used are:
- Password storage: SM3 Hash is used to hash user passwords securely, protecting user credentials from being stolen.
- Digital signature: SM3 Hash is used to generate digital signatures, ensuring that the message sender’s identity is not compromised.
- Data integrity verification: SM3 Hash is used to verify the consistency of data by comparing the hash value of the original data and the received data.
Misconceptions and FAQs
Misconception: SM3 Hash is less secure than other hash functions.
This is a misconception. SM3 Hash has the same or even better security than other hash functions like SHA-3.
FAQ 1: Can SM3 Hash be reversed?
No, SM3 Hash is a one-way function. It is computationally infeasible to determine an input message from its digest.
FAQ 2: Should I use SM3 Hash instead of SHA-3?
It depends on the application requirements. If you require compliance with Chinese cryptographic regulations, SM3 Hash is a better choice. Otherwise, SHA-3 is more widely used and has better hardware performance.
Conclusion
SM3 Hash is a robust and secure cryptographic hash function with features like collision resistance, pre-image resistance, and an iterative compression function. SM3 Hash is widely used in password storage, digital signature, and data integrity verification. Understanding SM3 Hash is fundamental for developers to ensure data security in various scenarios.
Reference Links:
