Introduction
Data security is crucial in modern-day communication systems, and assuring that messages are not modified or tampered with in transmission is essential. HMAC-HAS160 Hash is a cryptographic algorithm that provides message authentication by ensuring message integrity using a secure hashing mechanism.
In this article, we will delve into the basics of the HMAC-HAS160 Hash algorithm, explaining how it works, key features, scenarios that developers can use it in, alongside common misconceptions and FAQs.
What is HMAC-HAS160 Hash?
HMAC-HAS160 Hash is a cryptographic algorithm that provides message authentication by ensuring message integrity using a secure hashing mechanism. HMAC stands for Hash-Based Message Authentication Code, while SHA-1 (Secure Hash Algorithm) or HAS-160 is the hashing algorithm used.
The HMAC-HAS160 Hash algorithm provides an extra layer of security to ensure only authorized parties can access a message, data, or file. It relies on a message’s fixed-length hash value to verify its integrity and authenticity during transmission.
How it works
HMAC-HAS160 Hash algorithm works by taking a message, adding a secret key to it and hashing it, creating a fixed-length hash. The resulting hash is then sent alongside the message to the receiver.
When the receiver gets the message and hash, the algorithm repeats the process with the same key, and if the hash value is identical to the previous one received, it confirms message integrity, meaning the message has not been tampered with.
Scenarios of use
Developers can use HMAC-HAS160 Hash algorithm in a variety of scenarios, including:
- Secure communication in web applications
- Secure data transmission in IoT devices
- Password verification and security in login authentication systems
- Secure file transfer and exchange
Key features
The HMAC-HAS160 Hash algorithm has the following key features:
- Provides message authenticity and integrity
- Uses a fixed message length hash value
- Uses a secret key for additional security
- Provides secure hashing to prevent data tampering or theft
Misconceptions and FAQs
Misconception 1: HMAC-HAS160 Hash algorithm is encryption.
HMAC-HAS160 Hash algorithm is not encryption. While encryption ensures data confidentiality by making it unreadable, hashing makes it possible to confirm message integrity by verifying the message was not tampered with.
Misconception 2: HMAC-HAS160 hashing is reversible.
HMAC-HAS160 hashing is not a reversible process. Once the message is hashed, it creates a one-way hash value that cannot be converted back to the original message.
FAQ 1: Is HMAC-HAS160 Hash algorithm secure?
Yes, HMAC-HAS160 Hash algorithm is secure. It provides message authenticity and integrity, meaning that messages or data cannot be tampered with during transmission.
FAQ 2: Can I use HMAC-HAS160 Hash algorithm in my application?
Yes, you can use HMAC-HAS160 Hash algorithm in your application. Many programming languages have built-in libraries for both HMAC and SHA-1 hashing, so you won’t have to develop the algorithm from scratch.
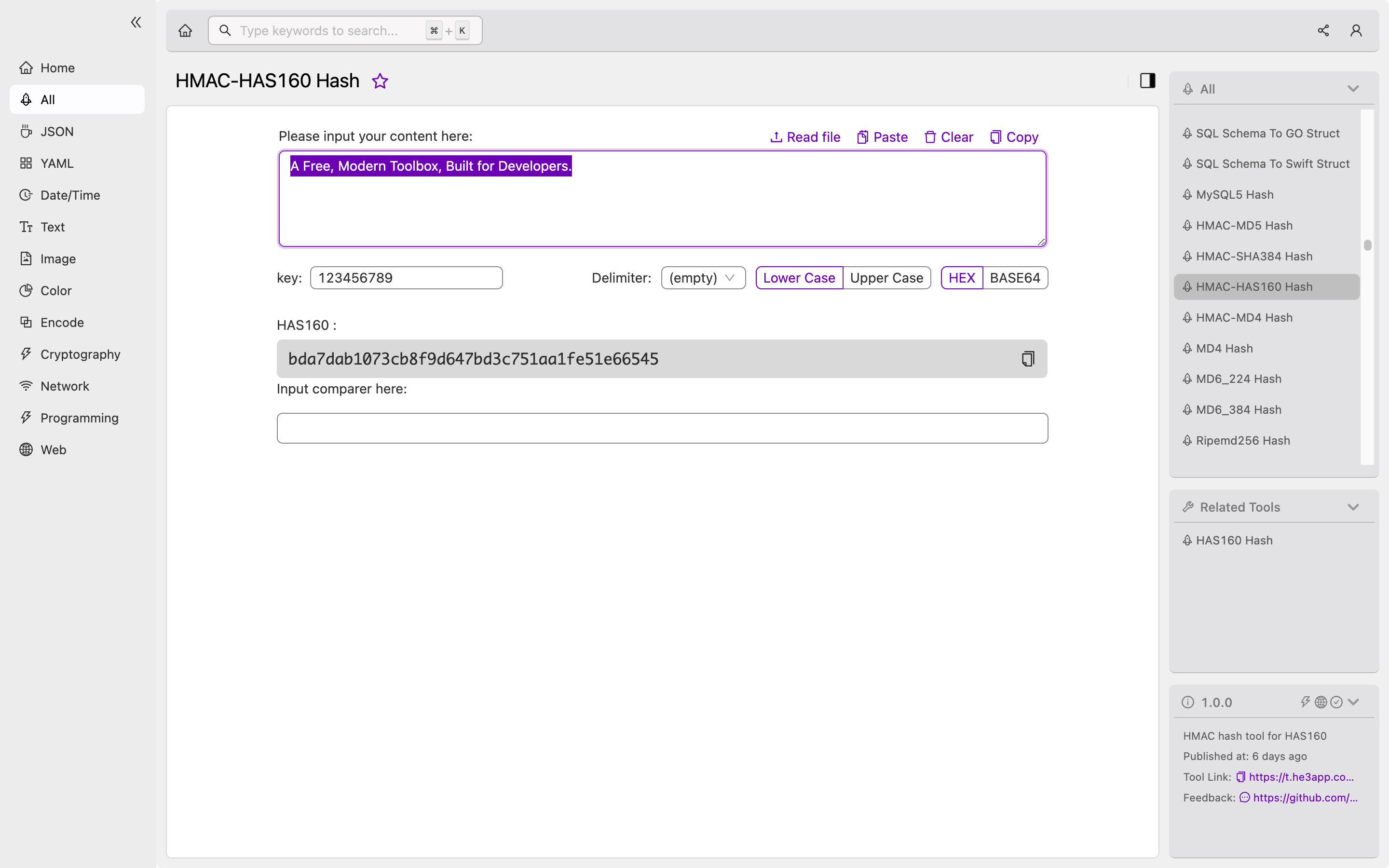
How to Use HMAC-HAS160 Hash Tool
Or you can use HMAC-HAS160 Hash tool in He3 Toolbox (https://t.he3app.com?wb5u) easily.
Conclusion
HMAC-HAS160 Hash is an essential cryptographic algorithm that provides message authentication by ensuring message integrity using a secure hashing mechanism. It is a widely accepted algorithm for secure communication in modern-day web applications, IoT devices, and password verification authentication systems.
In conclusion, HMAC-HAS160 Hash algorithm provides an added layer of security essential in modern-day communication systems. Developers must understand its basic concepts, key features, scenarios of use, misconceptions and FAQs, to fully harness its capabilities.
