Introduction
In today’s digital world, data security is more important than ever. There are many ways for hackers and malicious actors to access and alter your files. One solution to ensure file integrity and prevent tampering is to use Check File Checksum. In this article, we’ll dive into the concept of file checksums, how they work, common misconceptions, and how developers can use them in their projects.
What is Check File Checksum?
A checksum is a small piece of data that results from a complex calculation performed on a larger piece of data. This calculation is called a hashing algorithm, and it creates a unique signature or fingerprint for a file. Checksums can be used to verify the integrity of a file, as even slight alterations to the file will result in a different checksum.
Check File Checksum is a tool that allows developers to easily generate and check checksums for their files. This tool supports different hashing algorithms such as MD5, SHA-1, and SHA-256.
How does it work?
To generate a checksum for a file, you can use the openssl command in the terminal. For example, to generate an MD5 checksum for a file named example.txt, you would run the following command:
openssl md5 example.txtThis will output the checksum for the file in hexadecimal format.
To check the integrity of a file, you would compare the checksum of the original file with the checksum of the file in question. If the checksums match, it’s likely that the file has not been tampered with.
Or you can use Check File Checksum tool in He3 Toolbox (https://t.he3app.com?0r0h) easily.
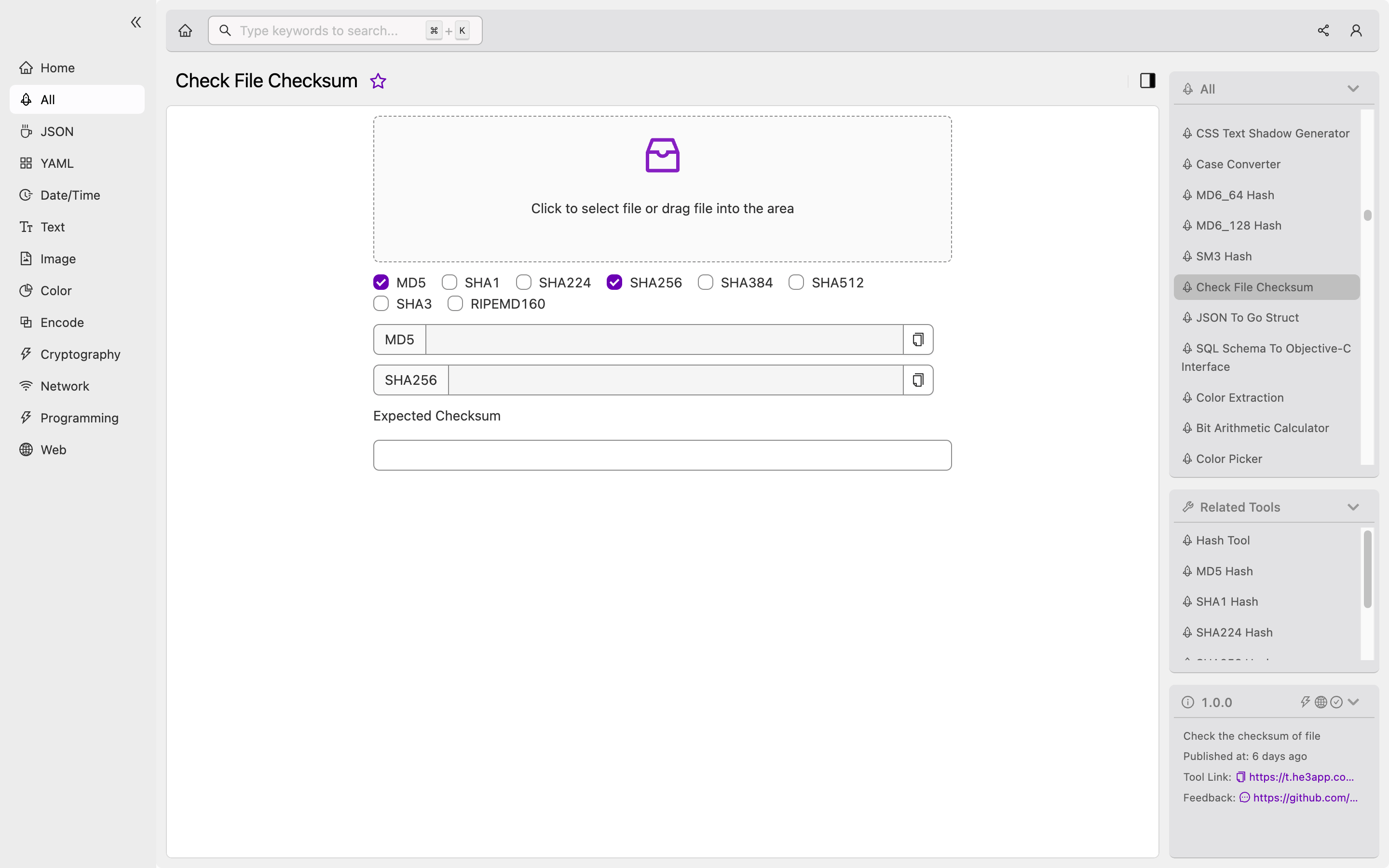
Key Features
Here are some key features of Check File Checksum:
| Feature | Description |
|---|---|
| Multiple hashing algorithms | Supports MD5, SHA-1, SHA-256, and other hashing algorithms. |
| Batch processing | Can process multiple files at once. |
| Comparison tool | Allows you to easily compare checksums for two files. |
| Cross-platform | Available on Windows, macOS, and Linux. |
Scenarios for Developers
Check File Checksum is a useful tool for developers in many scenarios. Here are some examples:
Code distribution
When distributing code to clients or other developers, it’s important to ensure that the code has not been tampered with. By including the checksum of the code in the distribution files, you can allow users to verify the integrity of the files they receive.
Database backups
When creating backups of databases, it’s crucial to ensure that the backup files have not been altered. By generating a checksum for the backup file and comparing it to the original database, you can ensure that the backup is accurate and complete.
Misconceptions and FAQs
Misconception: Checksums provide full security
Checksums can help ensure file integrity, but they do not guarantee full security. Malicious actors can still alter files if they have access to both the original file and the checksum.
FAQ 1: What is the best hashing algorithm to use?
The best hashing algorithm to use depends on your specific needs. MD5 is fast but has some security vulnerabilities, while SHA-256 is slower but more secure. SHA-3 is also a good option for those who want a balance between speed and security.
FAQ 2: Do I need to generate a new checksum for every file change?
Yes, you should generate a new checksum for every file change. As even slight alterations to the file will result in a different checksum.
Conclusion
Check File Checksum is a powerful tool for ensuring file integrity and preventing malicious file tampering. By generating and comparing checksums, developers can rest assured that their files are secure. We hope this guide has helped you understand the concept of file checksums and how to use them in your projects.
References:
