PGP Encryption (Pretty Good Privacy Encryption) is a popular encryption tool used to ensure secure communication. Developed by Phil Zimmermann in 1991, PGP Encryption uses a combination of symmetric-key and public-key cryptography to encrypt and decrypt messages.
How PGP Encryption Works
PGP Encryption uses a combination of symmetric-key and public-key cryptography to encrypt and decrypt messages. When a message is sent, it is first encrypted using a symmetric key algorithm, and then the symmetric key is encrypted using the recipient’s public key. The encrypted message and encrypted symmetric key are then sent to the recipient. The recipient decrypts the symmetric key using their private key and then uses the symmetric key to decrypt the message.
Here is an example of using PGP Encryption to encrypt a message:
$ gpg --output encrypted_message.pgp --recipient recipient@example.com --encrypt message.txtTo decrypt the message, the recipient would use their private key to decrypt the symmetric key and then use the symmetric key to decrypt the message:
$ gpg --output decrypted_message.txt --decrypt encrypted_message.pgpScenarios for Developers
Developers can use PGP Encryption to ensure secure communication in their applications. PGP Encryption can be used to encrypt sensitive data such as login credentials, credit card information, and personal information. Developers can also use PGP Encryption to encrypt email messages and attachments.
Key Features
PGP Encryption has several key features that make it a popular encryption tool:
- End-to-end encryption: Ensures that only the sender and recipient can read the message.
- Digital signatures: Ensures that the message has not been tampered with and comes from a trusted source.
- Key management: Allows users to manage their public and private keys.
- Cross-platform: Available on Windows, macOS, Linux, and other platforms.
Misconceptions and FAQs
Misconception #1: PGP Encryption is only for email communication.
PGP Encryption can be used to encrypt and decrypt any type of data, not just email messages.
Misconception #2: PGP Encryption is unbreakable.
While PGP Encryption is a strong encryption tool, it is not completely unbreakable. As computing power increases, it may become easier to break the encryption. However, PGP Encryption is currently considered to be a secure encryption tool.
FAQ #1: Can I use PGP Encryption for file encryption?
Yes, PGP Encryption can be used to encrypt and decrypt any type of file.
FAQ #2: Can I use PGP Encryption for instant messaging?
Yes, PGP Encryption can be used to encrypt and decrypt instant messages.
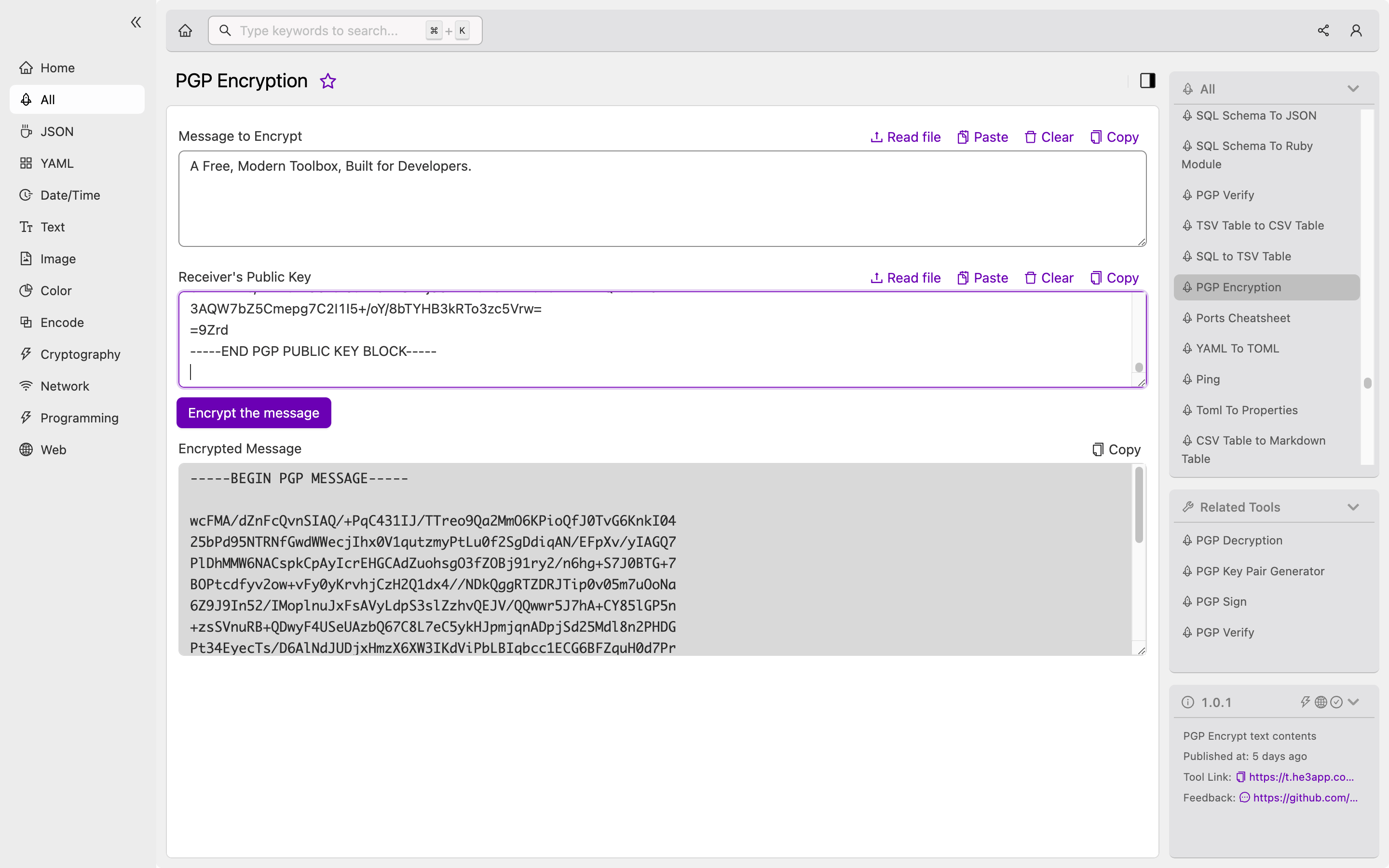
How to Use PGP Encryption in He3 Toolbox
Or you can use PGP Encryption tool in He3 Toolbox (https://t.he3app.com?sw7g) easily.
Conclusion
PGP Encryption is a powerful encryption tool that developers can use to ensure secure communication in their applications. By encrypting sensitive data and messages, developers can help protect their users’ privacy and security. For more information on PGP Encryption, see the Wikipedia page.
