Understanding JWT Generator for Developers”
As a developer, it’s important to understand authentication and security protocols for web development. JSON Web Tokens or JWTs are a widely-used open standard for transmitting information between parties as a JSON object. JWTs are used to securely authenticate users and protect sensitive data from malicious attacks. To generate and manage JSON Web Tokens, developers use JWT Generator.
How JWT Generator Works
A JWT consists of three parts: a header, a payload, and a signature. The header contains information about the token such as the algorithm used for signature, the type of token, and the algorithm used for signing the token. The payload contains the actual data or claims about the user, such as the user ID, email, and permissions. The signature is generated by hashing the header and payload, using a secret key. The secret key is known only by the server, and used to validate the signature by hashing the header and payload.
JWT Generator creates a JWT using a set of inputs such as secret key, payload, and header information. The secret key can be any string value that is known only to the server. The payload usually contains user data such as user ID, email, and other custom fields. The header information specifies the algorithm used for signing the token.
Or you can use JWT Generator tool in He3 Toolbox (https://t.he3app.com?pdze ) easily.
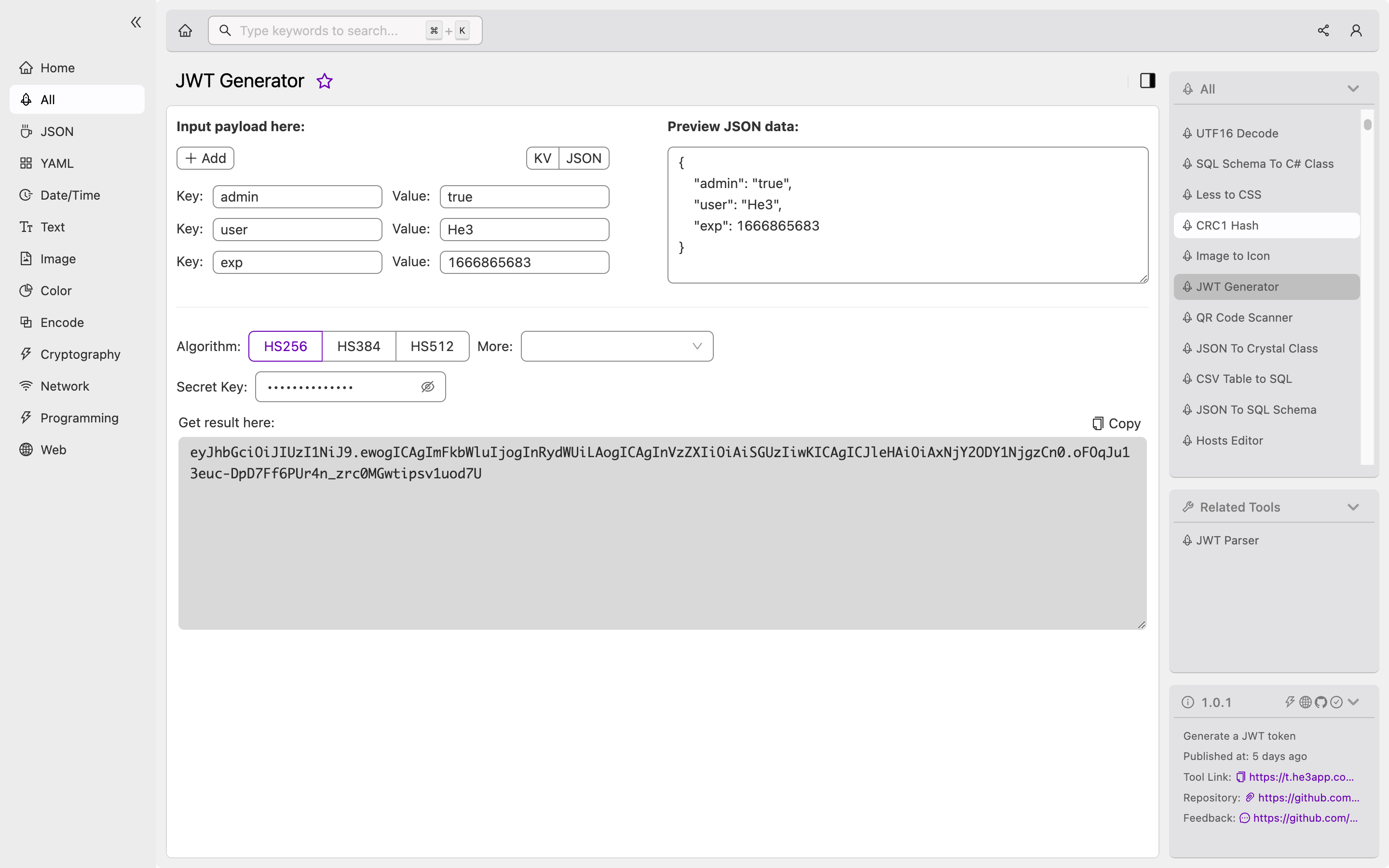
Scenarios of Using JWT Generator for Developers
JWTs are commonly used for authentication, authorization, and information exchange in web development. Developers use JWT Generator to generate tokens for user authentication, enabling them to securely transfer user data and make authorized API requests. JWTs can also be used in single sign-on (SSO) scenarios, allowing users to authenticate across multiple applications using the same token.
Key Features of JWT Generator
| Feature | Description |
|---|---|
| Customizable Payload | Developers can add custom fields to the payload to store user information such as name, email, or roles. |
| Header Information | JWT Generator allows developers to specify the algorithm used for signing the token, enhancing security. |
| Secret Key Management | Developers can use any string value as a secret key, providing flexibility and security options. |
Misconceptions and FAQs
Myth: JWTs are encrypted
JWTs are not encrypted, only the signature is hashed to ensure the integrity of the token. The payload can be read by anyone with access to the token, as it is base64 encoded, but not encrypted.
Myth: JWTs are always secure
While implementing JWTs for authentication and authorization, developers still need to handle security considerations such as cross-site scripting attacks (XSS) and cross-site request forgery (CSRF) attacks.
FAQ 1: Can I store sensitive data in the payload?
No, it’s not recommended to store sensitive data in the payload as it can be read by anyone with access to the token. Sensitive data should be encrypted separately, and only the encrypted data should be included in the payload.
FAQ 2: How often should the secret key be changed?
The secret key should be changed as often as necessary to maintain security. Best practice is to change the key at least every 6 months, or anytime an authorized user leaves the company.
Conclusion
JWT Generator is a powerful tool for developers to generate and manage JSON Web Tokens for authentication and security in web development projects. By understanding how JWTs work and the key features of JWT Generator, developers can create secure, customizable, and efficient authentication mechanisms for their web applications.
References: