Understanding Hash Tool for Developers
As a developer, you may have heard about hashing and encryption. Hashing is a process of converting data or text into a fixed-size representation, while encryption refers to transforming data using an algorithm to prevent unauthorized access to the information. Hash Tool is a program that assists developers in carrying out hashing and encryption tasks. In this article, we will dive deeper into Hash Tool and its application in cryptography.
How Hash Tool Works
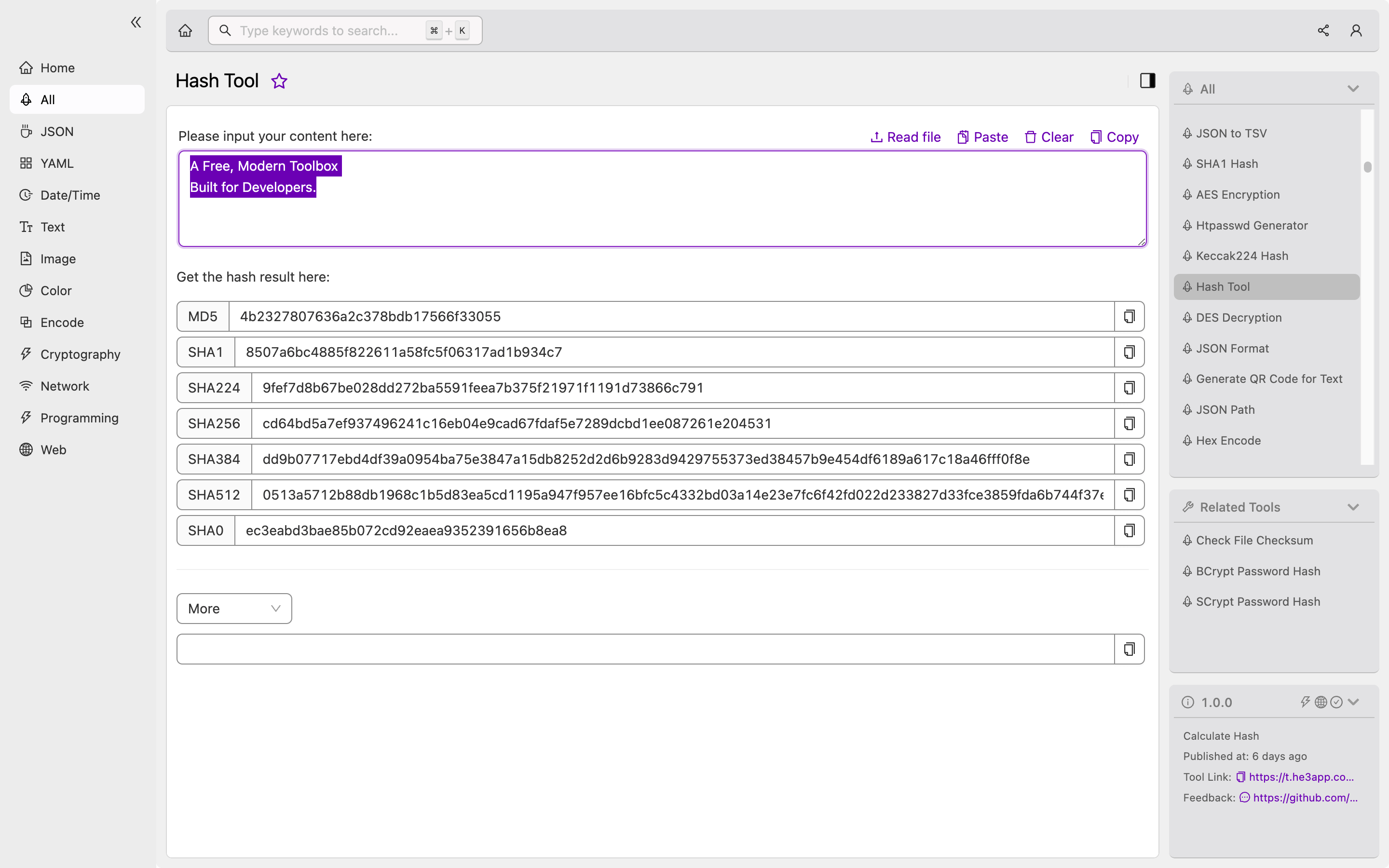
Hash Tool provides a graphical user interface for developers to perform hashing and encryption tasks. The program supports various algorithms like SHA-256, SHA-512, SHA-3, and BLAKE2. It is also flexible and can be used to hash passwords, files, or texts.
To use Hash Tool, developers can install the program on their computers, and then launch the program’s interface. After starting the tool, developers can select the type of hashing algorithm, input the information they want to hash, and provide any additional options. The tool then performs the hash function, and the output is displayed in the interface. It is a straightforward process.
Or you can use Hash Tool tool in He3 Toolbox (https://t.he3app.com?d8c1 ) easily.
Scenarios for Developers
Developers can use Hash Tool for many purposes. The program can help them in the following scenarios:
-
Password storage: Hash Tool can be used to secure passwords during storage. Instead of saving passwords in plain text or using weak encryption mechanisms, passwords can be hashed using a secure algorithm like SHA-256.
-
Data security: Hash Tool can help developers ensure data privacy, using its encryption capability. Files, messages, or any sensitive information can be transformed using encryption, and only users with the decryption key can access the content.
-
File integrity: Developers can use hash functions to check the integrity of their files. Hashing a file before and after transfer or edit, and comparing the hash values ensures that the file has not been tampered with or corrupted.
Main Features
Hash Tool has several key features that make it a popular tool among developers. Some of its features include:
| Feature | Description |
|---|---|
| User-friendly interface | Hash Tool provides a user-friendly interface that simplifies the hashing and encryption process. |
| Multiple algorithms | The program supports various hashing and encryption algorithms like SHA-256, SHA-512, SHA-3, and BLAKE2. |
| Customization | The tool allows developers to customize hashing options like salt and iterations. |
| Cross-platform | Hash Tool is compatible with Windows, macOS, and Linux operating systems. |
| Open-source | The tool is open-source, making it easier for developers to customize it to their needs. |
Misconceptions and FAQs
Misconception: Hashing and encryption are the same things.
Hashing and encryption perform different actions. Hashing is converting a message into a fixed-size string, while encryption is transforming the original message into a coded version that cannot be understood without a decryption key.
FAQ 1: I have a hashed password; can it be decrypted?
A hashed password cannot be decrypted. Hashing is a one-way function, so you cannot retrieve the original message from a hash.
FAQ 2: Does changing even one character in a file affect its hash value?
Yes, changing even one character in a file changes its hash value. Hash functions are sensitive to even the slightest changes.
Conclusion
Hash Tool is a handy tool for developers to perform hashing and encryption tasks. The program is flexible, user-friendly, and supports various algorithms. Developers can use it to enhance data privacy, file integrity, and password security. To explore more about Hash Tool, see the Wikipedia article.