Introduction
When it comes to web development, security should be a top priority. One of the most common security issues developers encounter is related to password storage. BCrypt Validator is a hashing tool that provides developers with a secure way to store and manage passwords. In this article, we will discuss the concept of BCrypt Validator, its key features, usage scenarios, misconceptions, and FAQs.
What is BCrypt Validator?
BCrypt is a password-hashing algorithm that uses a key factor to provide developers with a secure way to store passwords. It works by generating a random salt and combines it with the given password to create a hash. The resulting hash can only be decrypted using the original password or comparing the hash to a new one generated with a user input. BCrypt Validator makes it easier for developers to implement this security measure, ensuring secure password storage.
Key Features
BCrypt Validator offers several key features that make it the preferred method for password hashing. These features include:
- Key factor: The number of times the algorithm runs, adding extra complexity to the password.
- Salting: Providing a random salt each time a password is hashed ensures no two hashes are the same, even if the passwords are identical.
- No length limit: Unlike other hashing algorithms, there is no limit to the length of passwords that can be hashed.
- Resistance to brute-force attacks: BCrypt is able to slow down brute-force attacks by requiring more computations each time a password is entered.
Scenarios
BCrypt Validator can be easily integrated into web applications to secure user passwords. It can work in most scenarios where password authentication is required—login systems for online banking, online shopping sites, social media sites, and many more. Developers can use it in PHP, Ruby, Java, and other languages that support the BCrypt algorithm.
How to Use BCrypt Validator
BCrypt can be used with a variety of languages and platforms. Here’s an example of implementing BCrypt in PHP and a quick way to use it without coding skills:
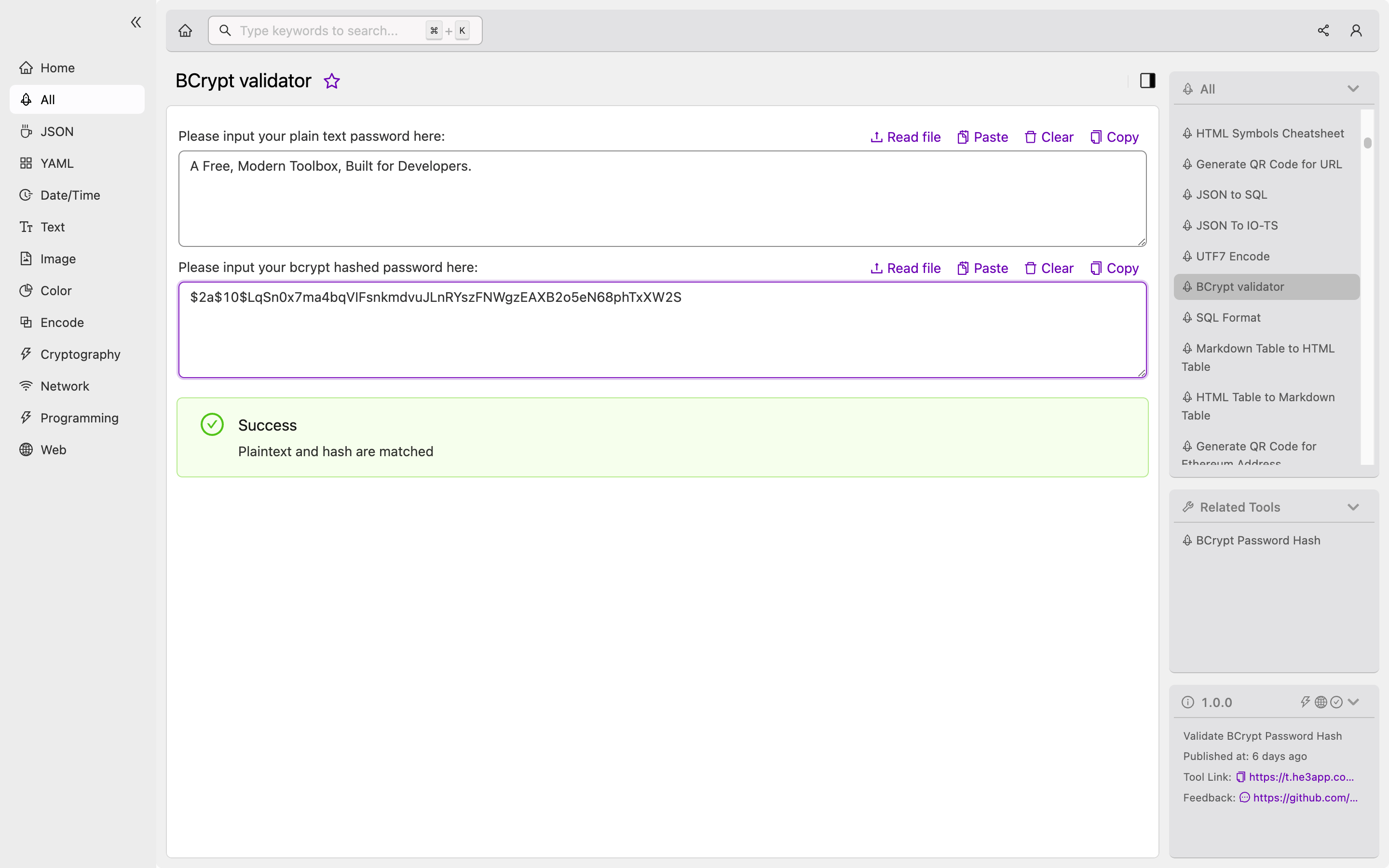
- Download and install He3 Toolbox (https://t.he3app.com?b236).
- Select “BCrypt validator” in the left column categories and enter your password in the Password field.
- The tool will generate the hashed password and the related salt (see the screenshot below).
Or you can use the following PHP code:
$password = 'myPassword';
$salt = password_hash($password, PASSWORD_BCRYPT);Misconceptions
Some misconceptions exist around BCrypt Validator, here are two of them:
- BCrypt’s default key factor is too low to be secure: BCrypt’s default key factor is 10. However, this is still enough to ensure that the hash will take too long for an attacker to brute force. BCrypt allows you to increase the key factor to make brute-force attacks more difficult.
- BCrypt is too slow to use: BCrypt is computationally expensive, which is a feature, rather than a drawback. The computation speed slows down brute-force attacks, requiring more computational time to guess the original password.
FAQs
Here are some frequently asked questions about BCrypt Validator:
Q: What makes BCrypt Validator different from other hashing algorithms?
A: BCrypt Validator is designed to be slow and computationally expensive, making brute-force attacks more difficult. Additionally, it provides a key factor that can be increased to add an additional layer of security.
Q: Can I use BCrypt to encrypt other data besides passwords?
A: BCrypt is designed for hashing passwords, and it should not be used to encrypt other sensitive data.
In conclusion, BCrypt Validator is an essential tool for securing user passwords in any web application. By providing features like salting, key factor, and resistance to brute-force attacks, it makes it difficult for attackers to retrieve user passwords. Whether you are a seasoned developer or a beginner, BCrypt Validator can help you to ensure that your web projects are secure.
Reference links: