Introduction
One of the critical aspects of cybersecurity is ensuring secure communication by maintaining privacy and confidentiality. Encryption plays a significant role in achieving this goal. However, encryption is not effective without decryption, and that’s where Aes Decryption comes in. In this article, we’ll learn about what Aes Decryption is, how it works, scenarios of use, key features, misconceptions, and FAQs.
What is Aes Decryption?
Aes Decryption is a process that reverses the encryption process of Advanced Encryption Standard (AES) to convert the encrypted data into its original form. It is a cryptographic algorithm for securing data through encryption and decryption. Aes Decryption uses symmetric keys to make the data secure from unauthorized access, thereby maintaining confidentiality.
How Does Aes Decryption Work?
The AES algorithm comprises three key components: the encryption algorithm, the key expansion, and the decryption algorithm. The encryption algorithm transforms plaintext into ciphertext, whereas the decryption algorithm transforms ciphertext into plaintext.
The Aes Decryption process is relatively simple. The encrypted data and a key are provided as inputs to the decryption algorithm. The decryption algorithm performs a mathematical operation on the encrypted data, with the key acting as the input. The mathematical operation reverses the encryption function and restores the original plaintext data.
Below is sample code illustrating how to perform Aes Decryption in Python:
from Crypto.Cipher import AES
import base64
def aes_decrypt(ciphertext, key):
decrypted_data = AES.new(key, AES.MODE_CBC, 'This is an IV456').decrypt(base64.b64decode(ciphertext))
return decrypted_data.decode('utf-8')
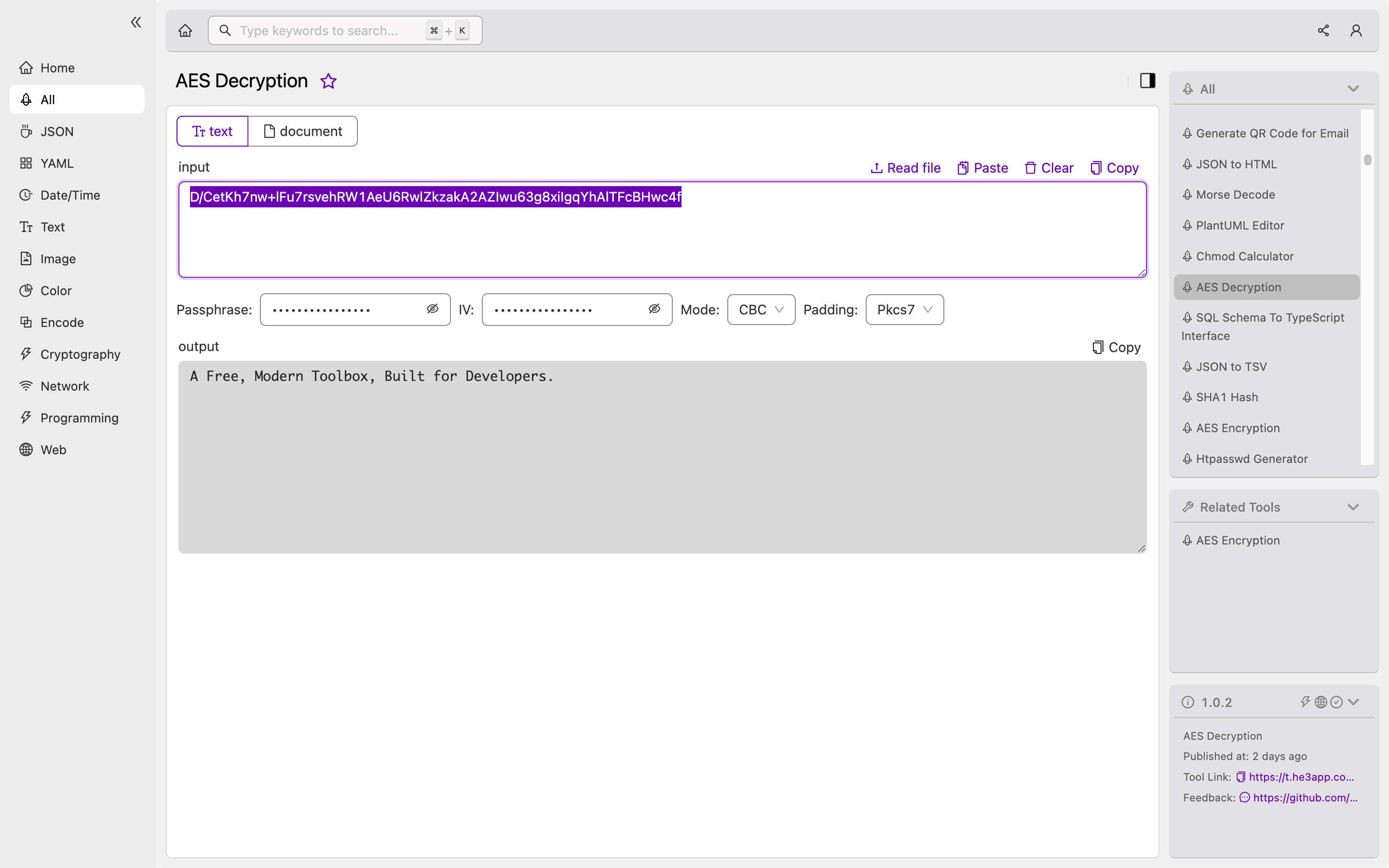
print(aes_decrypt('<encrypted-data>', '<key>'))Or you can use Aes Decryption tool in He3 Toolbox (https://t.he3app.com?fqmk ) easily.
Scenarios of Use for Developers
- Digital signatures: Developers use Aes Decryption to decrypt digital signatures to verify file integrity.
- Secure data transmission: Aes Decryption is an integral part of secure data transmission over the internet.
- Secure database backup: Developers use Aes Decryption to secure sensitive data backups in a database.
Key Features of Aes Decryption
- High level of security: Aes Decryption uses a 128 or 256-bit key, providing a high level of security.
- Efficient decryption: Aes Decryption is fast and efficient, even with large volumes of data.
- Compatibility: Aes Decryption is compatible with various environments, making it popular among developers.
Misconceptions about Aes Decryption
One common misconception about Aes Decryption is that it provides unbreakable security. Hackers and cybersecurity experts can use a variety of tools and techniques to bypass or break Aes Decryption. Moreover, the security of a system depends on various factors, including how the key is stored and how it is managed.
FAQs about Aes Decryption
Q: Is Aes Decryption the only way to secure data transmission over the internet? A: No, other cryptographic algorithms like RSA, Blowfish, and DES can also secure data transmission over the internet.
Q: Can Aes Decryption secure data at rest? A: Yes, Aes Decryption can secure data backups in databases and other data storage locations.
Q: Is Aes Decryption suitable for small-scale applications? A: Yes, Aes Decryption is suitable for both small-scale and large-scale applications.
Conclusion
Aes Decryption is a critical aspect of cybersecurity that developers should familiarize themselves with to secure sensitive data. Aes Decryption uses a mathematical operation to reverse the encryption process and restore the original plaintext data. Programmers can use various programming languages to implement Aes Decryption. Always remember, Aes Decryption is not invincible, and developers should layer their security strategies to ensure optimal protection.