Exploring SHA256 Hash Algorithm: A Beginner’s Guide
Security is a major concern when it comes to data transmission and storage. One of the ways to ensure data security is to use cryptography to encode the data so that it can be read only by authorized persons. One of the vital components of modern cryptography is hashing algorithms.
Hashing algorithms convert data of arbitrary size to a fixed-size digest. This makes it easy to compare the digest rather than the entire data. SHA256 Hash Algorithm is one of the most popular and secure hashing algorithms out there. In this article, we will explore the basic concept of the SHA256 hash algorithm.
What is SHA256 Hash Algorithm?
Secure Hash Algorithm (SHA) is a set of cryptographic hash functions designed by the National Security Agency (NSA). SHA256 is one of the popular algorithms in the SHA series, which produces a 256-bit hash value (digest) that is unique to the input data. This algorithm is a one-way function, meaning that once the hash value is generated, the initial message cannot be obtained from it.
To generate a SHA256 hash, a message is fed into the algorithm, and an output digest (hash value) of 64 characters is generated, which is a fixed size for SHA256. It is essential to note that even a small change in the input message results in a completely different output hash value.
How Does SHA256 Hash Algorithm Work?
SHA256 Hash Algorithm works by employing mathematical transformations and a series of logical operations, including bitwise operations, modular arithmetic, and Boolean logic, to convert the input message into a fixed-size hash value of 256 bits. Generally, the following steps are involved:
- Message Padding: Add padding bits to the message to ensure that its length is a multiple of 512 bits.
- Initialize Hash Values: Set the initial hash value to eight 32-bit words.(constants derived from the fractional parts of the cube roots of the first 64 prime numbers)
- Process the Message in Blocks: The message is divided into blocks of 512 bits, and each block is processed one at a time.
- Compute Hash Values: To compute the hash value for each block, a set of logical and arithmetic operations are performed on the previous hash value.
- Concatenate: The resulting 256-bit hash value is the concatenation of the eight 32-bit hash values.
How Can Developers Use SHA256 Hash Algorithm?
SHA256 Hash Algorithm is widely used in many industries and applications. Developers can use SHA256 Hash Algorithm to secure sensitive data and passwords, verify the integrity of files, and generate digital signatures.
Here’s some sample code in Python to generate a SHA256 Hash:
import hashlib
message = "Hello, World!"
hash_object = hashlib.sha256(message.encode())
hex_dig = hash_object.hexdigest()
print(hex_dig)Or you can use SHA256 Hash tool in He3 Toolbox ( https://t.he3app.com?aj1p) easily.
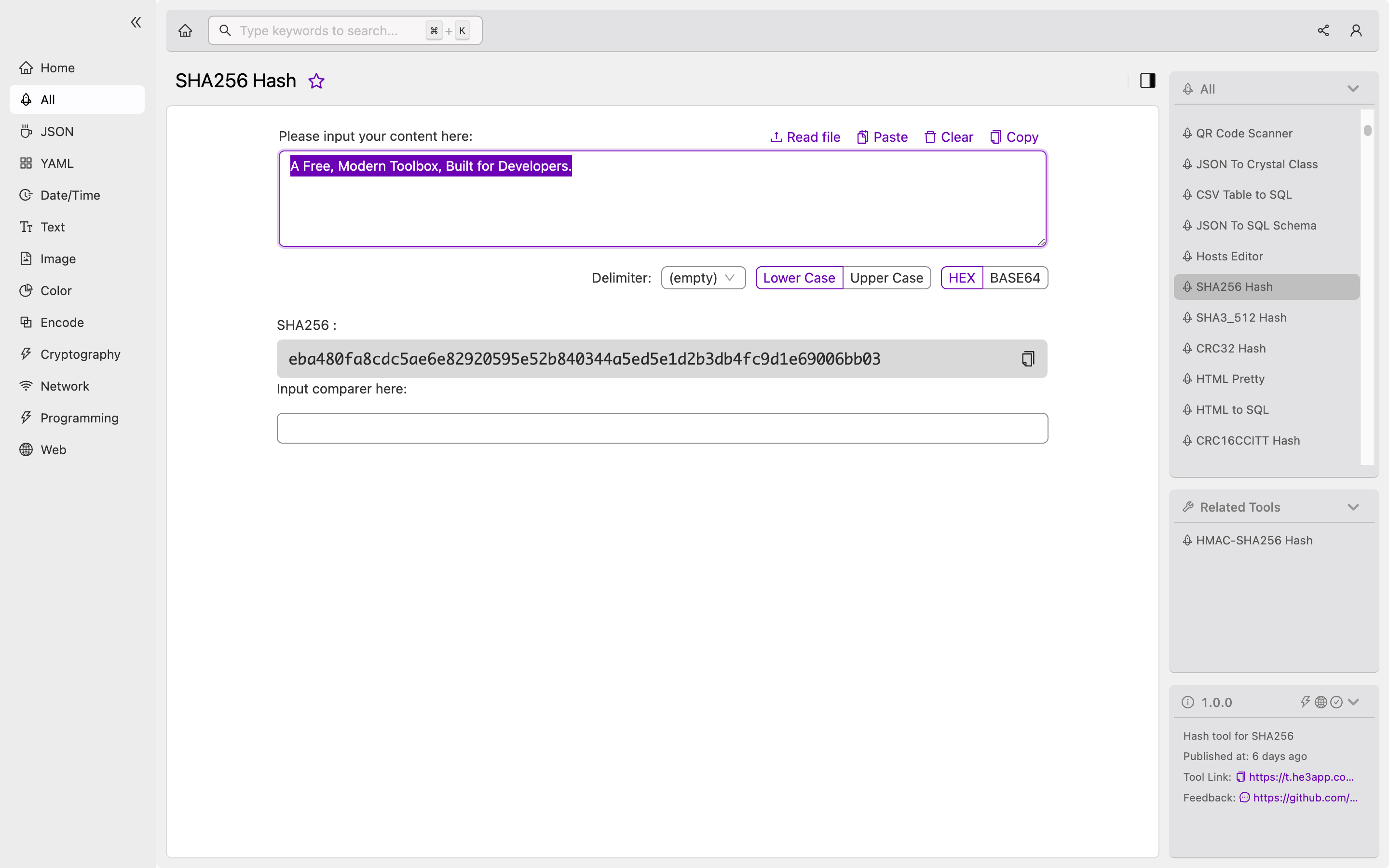
Key Features
Some of the key features of SHA256 Hash Algorithm include:
- Collision Resistance: It is computationally infeasible to find two different messages that produce the same hash value.
- Deterministic: The hash function always produces the same output for the same input.
- Fixed-Size Output: The output digest is always of fixed size (256 bits).
- One-Way Function: The input message cannot be derived from the hash value.
Misconceptions and FAQs
Misconceptions
There are some misconceptions about SHA256 Hash Algorithm. Here are some of them:
- SHA256 Hash Algorithm is not encryption. It is a one-way function that converts the input into a fixed-size digest.
- SHA256 Hash Algorithm cannot ensure data secrecy. If someone gets access to the hash value, they cannot retrieve the initial message. Still, they can guess it by hashing millions of different inputs until the hash value matches.
- SHA256 Hash Algorithm is not vulnerable to all types of attacks. Quantum computers have the potential to break SHA256 Hash Algorithm.
Frequently Asked Questions
Here are some frequently asked questions about SHA256 Hash Algorithm:
Q: How long is the SHA256 hash value?
A: The SHA256 hash value is a fixed-size digest of 256 bits or 64 characters.
Q: What is the difference between SHA256 and SHA-3?
A: SHA256 is a part of the SHA-2 family of hash algorithms, while SHA-3 is a separate family of hash algorithms. SHA-3 is designed to be more robust against certain types of attacks than SHA-256.
Q: Is SHA256 secure enough?
A: SHA256 is still considered to be secure and widely used in many applications. Although, there can be more potent attacks in the future.
Conclusion
In conclusion, SHA256 Hash Algorithm plays an essential role in ensuring data security. Developers can use SHA256 Hash Algorithm to secure passwords, data, verify the integrity of files, and generate digital signatures. SHA256 Hash Algorithm provides a fixed-size digest that is unique to the input data, making it easier to compare the digest rather than the whole data. If you want to learn more about SHA256 Hash Algorithm, here are some useful links: